蓝队应急响应工具箱
这个工具已经更新好久了(老粉都用过,新粉丝再唠叨两句,哈哈哈哈哈哈哈哈),还没用上的师傅速看~
开发者: ChinaRan404,W啥都学,Code_200,清辉等
关注一波公众号:
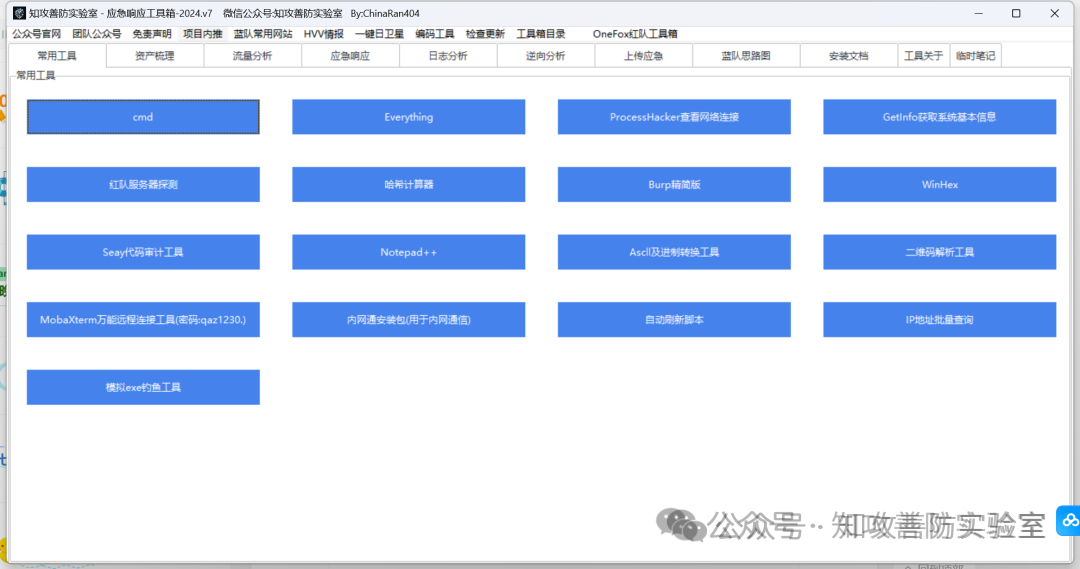
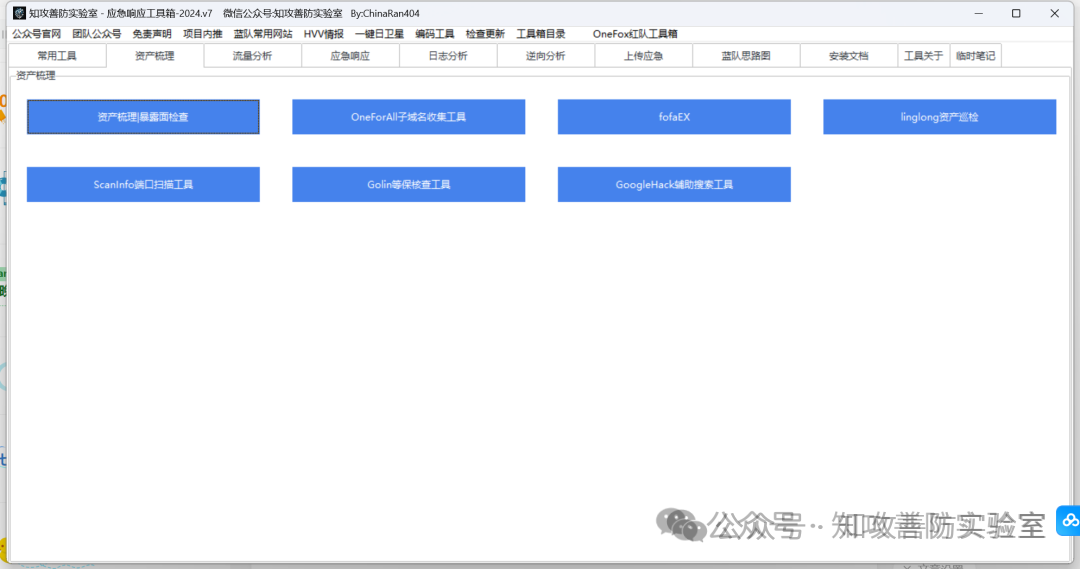
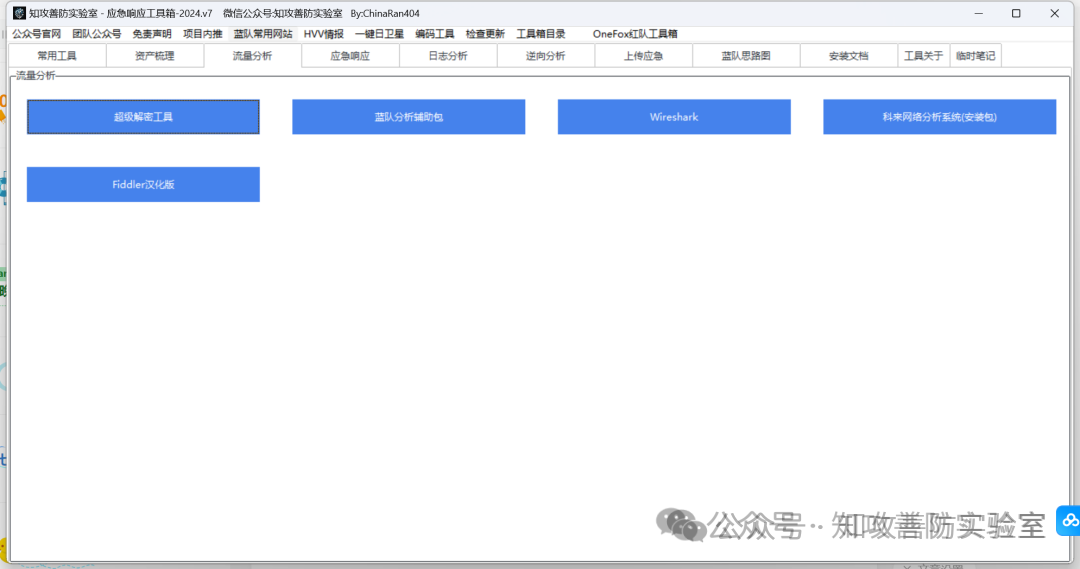
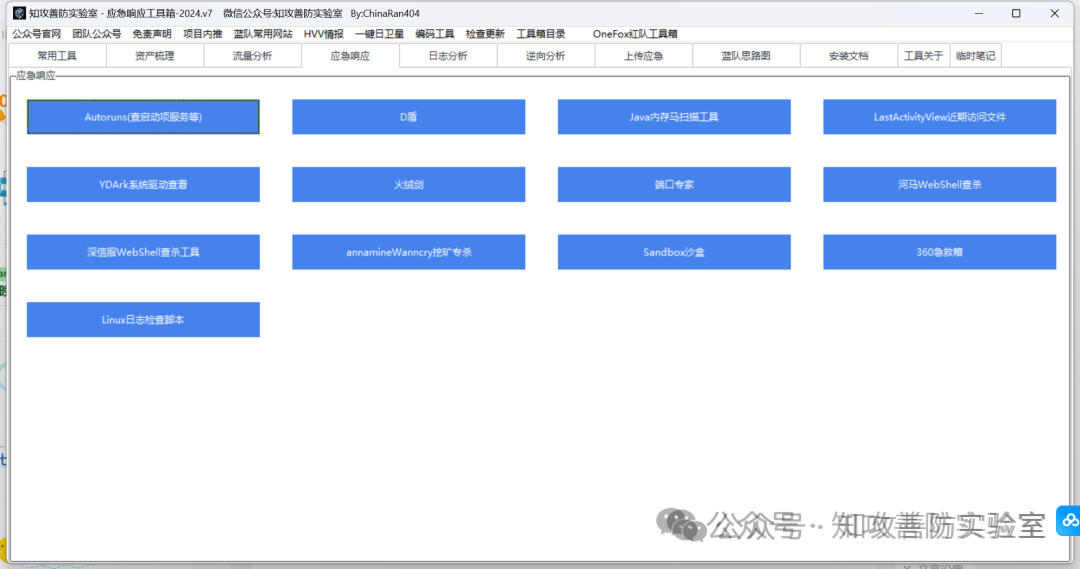
蓝队工具箱是为打造一款专业级应急响应的集成多种工具的工具集,
由真实应急响应环境所用到的工具进行总结打包而来,
由 ChinaRan404,W 啥都学,清辉等开发者编写.
把项目现场中所用到的工具连同环境一同打包,并实现“可移植性”“兼容性”“使用便捷”等优点。
集成模块:“常用工具”,“流量分析”,“应急响应”,“日志分析”,“逆向分析”,,“上传应急”,“蓝队思路图”,”安装文档“,“临时笔记”等 9 个模块。
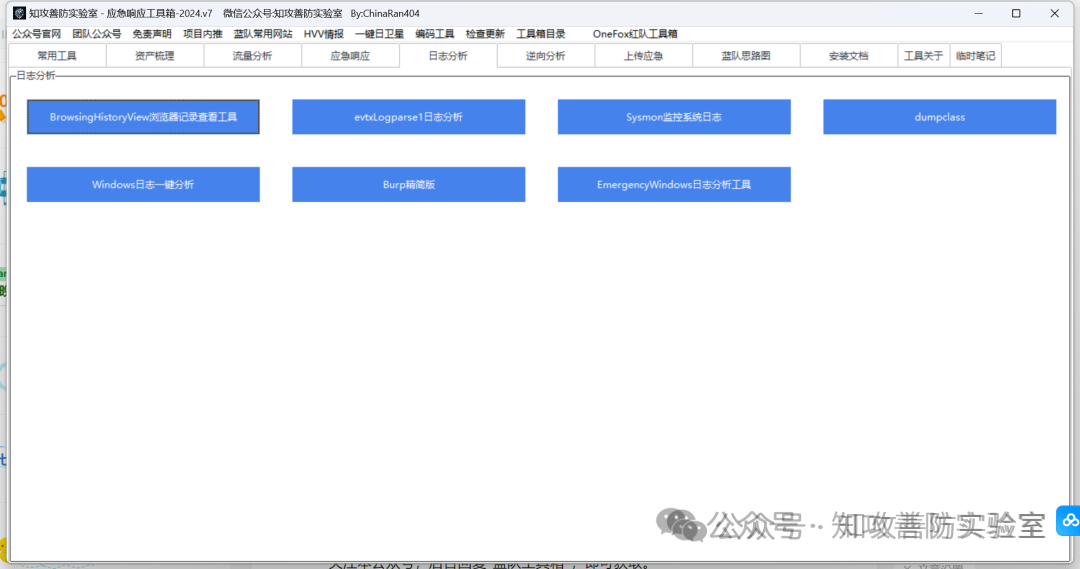
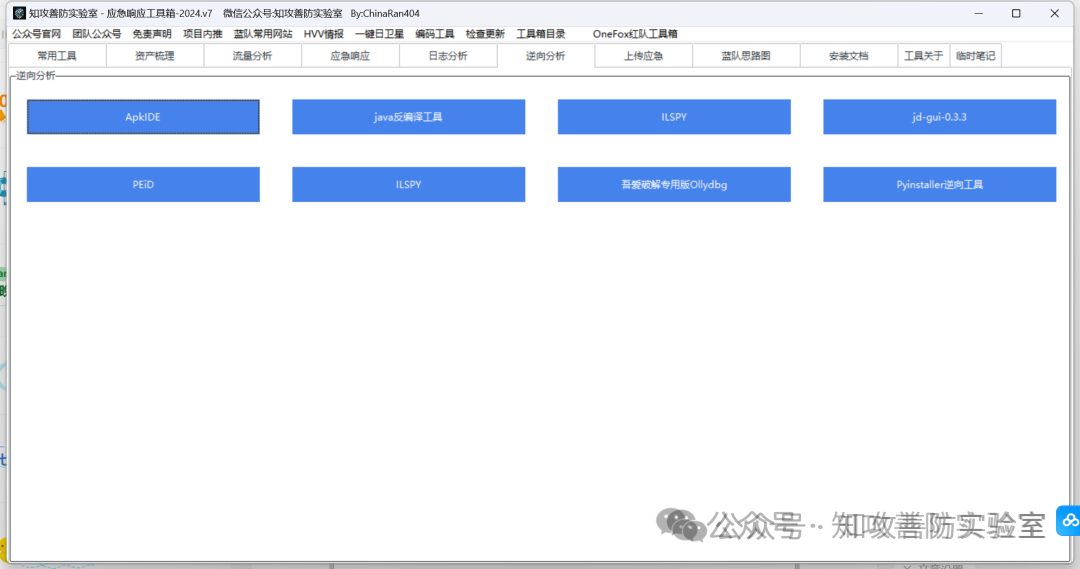

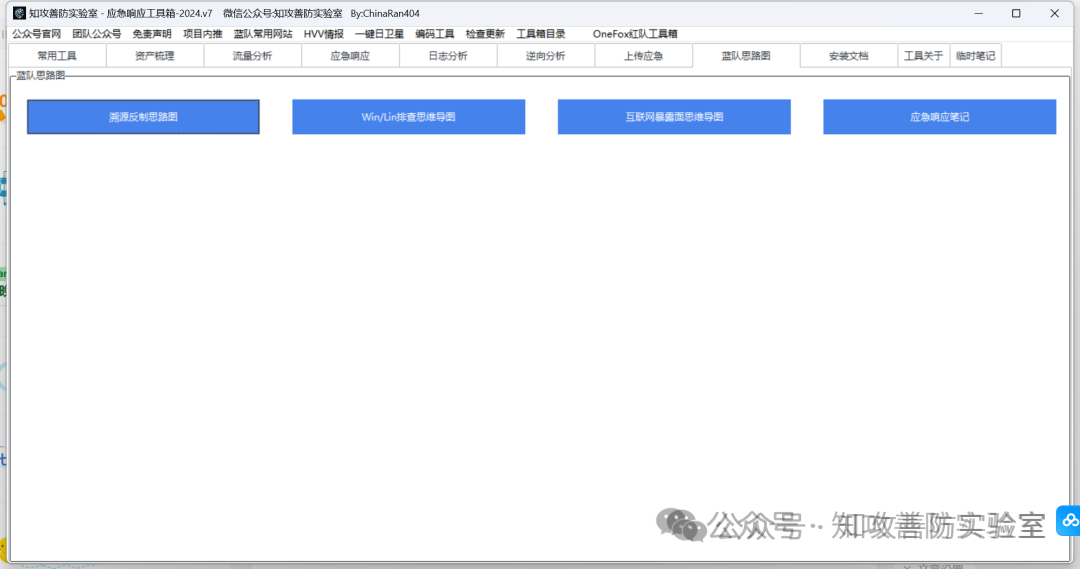
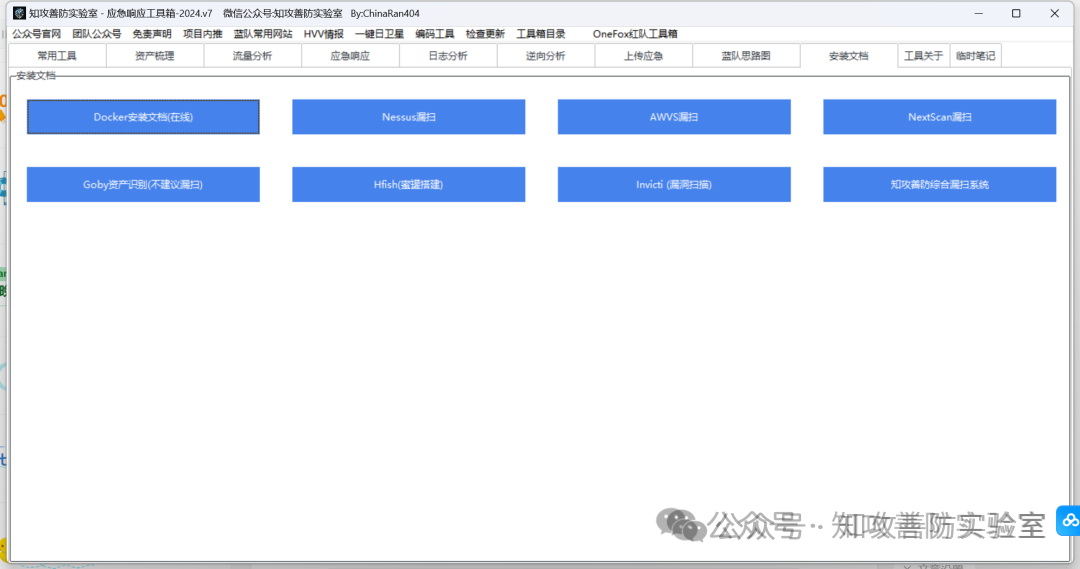
下载地址
后台回复:"蓝队工具箱"即可
Tips:
考证咨询:全网最低最优惠报考NISP/CISP/CISSP/PTE/PTS/IRE/IRS
等证书,后台回复“好友”加V私聊。
往期推荐
[
【攻防演练】泛微 e-cology 9 远程命令执行漏洞
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247501010&idx=1&sn=2ec6e2e708109ebdbb07de0465cf0b18&chksm=c0c86526f7bfec30d65ebf551d1beb79464754ed6a8037136ea5f92b02d68aec149a3e2fd2a3&scene=21#wechat_redirect)
[
【RCE-0day】最新NACOS 漏洞复现
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247501004&idx=1&sn=d243a5246ef491bf5daeee79c471a39d&chksm=c0c86538f7bfec2e087f0cefad938b8b4224cbdb0de0cb627f283a4ac4cf4655e5bd6d3aed31&scene=21#wechat_redirect)
[
揭秘色情APP取证:最全视频固定技巧指南
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500997&idx=1&sn=6d6e4988788f63b86b0ce1c1e958c3c0&chksm=c0c86531f7bfec273052e5472dd36ee405140a1a691ebf48f601b98068086c6ec91741edb213&scene=21#wechat_redirect)
[
FastJson全版本Docker漏洞环境
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500984&idx=1&sn=3a5f714017cf013e212aee1e7f4fac7c&chksm=c0c8654cf7bfec5adf78da105e905c56b79f3a2514192aaa4543e7cee759fc953b52e3c60e52&scene=21#wechat_redirect)
[
【2024hvv】末班车、捡漏群
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500990&idx=1&sn=fa4b39cc29903026e1c0bc2503a6300b&chksm=c0c8654af7bfec5c454e32d11e8fd1775e9d6868db21010bdc95d693f238fe2904eaeefa5828&scene=21#wechat_redirect)
[
改造版hvv小脚本
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500966&idx=1&sn=4eeeb16aa2b015ad592d1ec46eac964b&chksm=c0c86552f7bfec440b6a79dd5ff62552e61105fa2e8b27b05cbdc377ec69f9967fb41346d883&scene=21#wechat_redirect)
[
SSH也能存在RCE?
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500940&idx=1&sn=abfdde11287b8dde44ad46a05cc07fba&chksm=c0c86578f7bfec6e55c3c2438910dbeb42b53ae08fbe911bf26bce2e25302dcf5f8eda327e11&scene=21#wechat_redirect)
[
CVE-2024-29943 Firefox RCE POC
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500924&idx=1&sn=b5a98881f71001a3c8d6cb923e53d9cd&chksm=c0c86588f7bfec9e2fb90d01e3ea657427b73a968e0a1c99427d5b0b5d1c504857dd57ea0fc6&scene=21#wechat_redirect)
[
【2024HW末班车】1500-4500需求中高级蓝队 20 名,签约赠送网络安全书籍或AI帐号
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500924&idx=2&sn=e6bf3bc52533e75f821ef77eae287e04&chksm=c0c86588f7bfec9ee9ab02d289e24a105cad046febf46feedaff6ceb10a31e9d986e9626610c&scene=21#wechat_redirect)
[
CVE-2024-1086 Linux提权漏洞利用与修复
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500875&idx=1&sn=443af7f4932a4d910f5a74ce51ed6bca&chksm=c0c865bff7bfeca92c341bc333feb145794374f98c183e059b6469f24df67e2ada49669dff0c&scene=21#wechat_redirect)
[
CVE-2024-26229 Windows 提权漏洞及 BOF 实现
](https://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247500868&idx=1&sn=82a25a352e622329a340f5686c0e5b84&chksm=c0c865b0f7bfeca68b876aead10cb1f444c031a9100d28d975540554061aa72223d3863f43ac&scene=21#wechat_redirect)
如果之前的log4j是核弹,这个漏洞算是中子弹?


点个「在看」你最好看
